SSH tunneling for secure communication and bypassing restrictions
SSH tunneling, an essential feature of secure communication, is an effective technique that significantly enhances online…

SSH tunneling, an essential feature of secure communication, is an effective technique that significantly enhances online…

In an era where secure communication is of utmost importance, tunneling TCP over ICMP using Ptunnel…

Packet capturing is an essential technique in network management, offering valuable insights into data flow, network…

Privilege escalation is a critical concept in cybersecurity, wherein attackers obtain elevated access to systems, often…

Hping3 is a robust network tool that extends beyond conventional packet crafting, enabling users to probe…

Linux is a powerful and versatile operating system that plays a critical role in penetration testing….

Ethical hacking is integral to protecting our digital environment by proactively identifying vulnerabilities before they can…

In the current digital landscape, understanding and mitigating security risks is more important than ever. Vulnerability…

Firewalls and Intrusion Detection Systems (IDS) are essential components in the protection of network security; however,…

In the current digital landscape, securing a WordPress site is of paramount importance. With the platform…

Subdomain enumeration is a fundamental technique in cybersecurity that aids in identifying potential vulnerabilities within a…

In today’s digital landscape, a comprehensive understanding of network reconnaissance, including host discovery, port scanning, and…
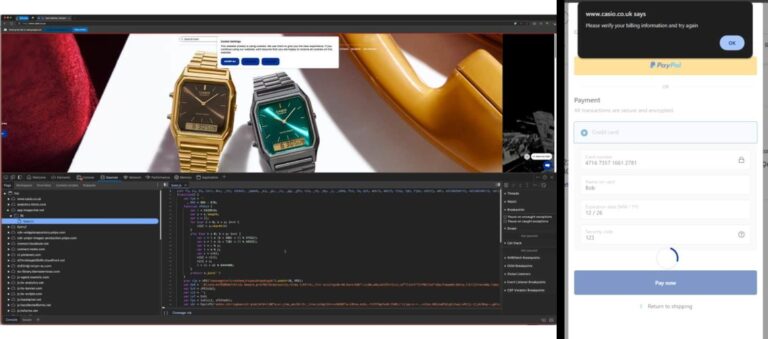
A recent investigation has revealed a significant web skimming campaign affecting at least 17 websites, including…
Feb 01, 2025Ravie LakshmananCybercrime / Fraud Prevention U.S. and Dutch law enforcement agencies have announced that…

☕Because everything in I.T. requires coffee: https://ntck.co/coffee Is it actually safe to run DeepSeek R1—or any…

☕Because everything in I.T. requires coffee: https://ntck.co/coffee Is it actually safe to run DeepSeek R1—or any…

DeepSeek had a database of your information just sitting there, exposed. DeepSeek, a Chinese artificial intelligence…

This company in India take advantage of people mis-dialling telephone numbers. They will be unclear about…