Wordlist generation and management with SecLists
In the world of cybersecurity, effective wordlist generation and management are crucial for successful security testing….

In the world of cybersecurity, effective wordlist generation and management are crucial for successful security testing….

// Membership //Want to learn all about cyber-security and become an ethical hacker? Join this channel…

// Membership //Want to learn all about cyber-security and become an ethical hacker? Join this channel…

Vulnerability / Threat Intelligence A previously undocumented backdoor named Msupedge has been put to use against…
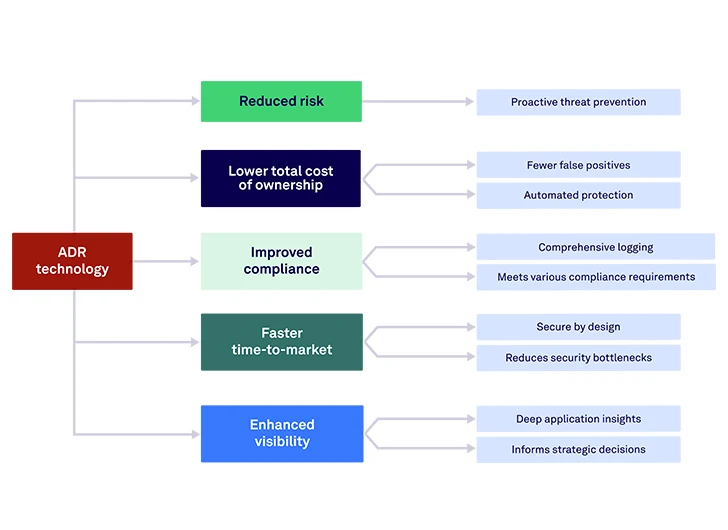
In today’s rapidly evolving cyber threat landscape, organizations face increasingly sophisticated attacks targeting their applications. Understanding…

Unlock Notion AI for $10 per month: https://ntn.so/networkchuckqna Unlock the power of AI to supercharge your…

In the ever-evolving landscape of cybersecurity, subdomain enumeration plays a crucial role in identifying potential vulnerabilities…
How Meta trained llama3.1 —-➝ https://juniper.net/theAImoment #junipernetworks #AImoment #meta

In the fast-paced world of ethical hacking, efficiency and organization are key to success. Tmux is…

The case against SolarWinds was filed by the Securities and Exchange Commission (SEC), a government agency…

Monitoring evolving DDoS trends is essential for anticipating threats and adapting defensive strategies. The comprehensive Gcore…

In the world of cybersecurity, proficiency with Linux commands can make all the difference for penetration…

In today’s fast-paced digital landscape, maximizing terminal efficiency can significantly boost productivity. This article explores the…

The U.S. Federal Bureau of Investigation (FBI) on Monday announced the disruption of online infrastructure associated…

In 2023, no fewer than 94 percent of businesses were impacted by phishing attacks, a 40…

The UK’s National Cyber Security Centre (NCSC) recently hosted an unprecedented conference at its London headquarters,…
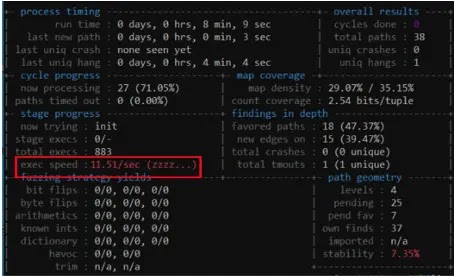
By reverse-engineering Quick Share’s proprietary communication protocol, researchers uncovered multiple vulnerabilities, including unauthorized file writes, forced…

U.S. authorities have arrested two believed administrators of the notorious WWH-Club, an online marketplace for stolen…