over 24,000 GPUs!!!
How Meta trained llama3.1 —-➝ https://juniper.net/theAImoment #junipernetworks #AImoment #meta
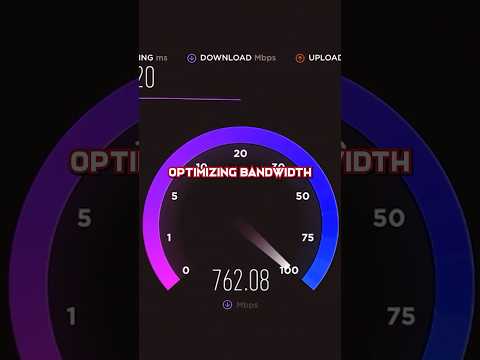
How Meta trained llama3.1 —-➝ https://juniper.net/theAImoment #junipernetworks #AImoment #meta

In the fast-paced world of ethical hacking, efficiency and organization are key to success. Tmux is…

The case against SolarWinds was filed by the Securities and Exchange Commission (SEC), a government agency…

Monitoring evolving DDoS trends is essential for anticipating threats and adapting defensive strategies. The comprehensive Gcore…

In the world of cybersecurity, proficiency with Linux commands can make all the difference for penetration…

In today’s fast-paced digital landscape, maximizing terminal efficiency can significantly boost productivity. This article explores the…

The U.S. Federal Bureau of Investigation (FBI) on Monday announced the disruption of online infrastructure associated…

In 2023, no fewer than 94 percent of businesses were impacted by phishing attacks, a 40…

The UK’s National Cyber Security Centre (NCSC) recently hosted an unprecedented conference at its London headquarters,…
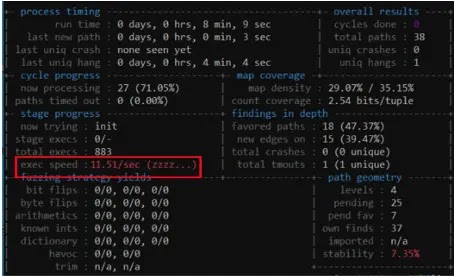
By reverse-engineering Quick Share’s proprietary communication protocol, researchers uncovered multiple vulnerabilities, including unauthorized file writes, forced…

U.S. authorities have arrested two believed administrators of the notorious WWH-Club, an online marketplace for stolen…

In today’s digital landscape, ethical hacking plays a crucial role in safeguarding information and systems from…

Cybersecurity researchers have discovered a new malicious package on the Python Package Index (PyPI) repository…

How do touchscreens work? Check out our new “Laptops and Mobile Devices” course, part of the…
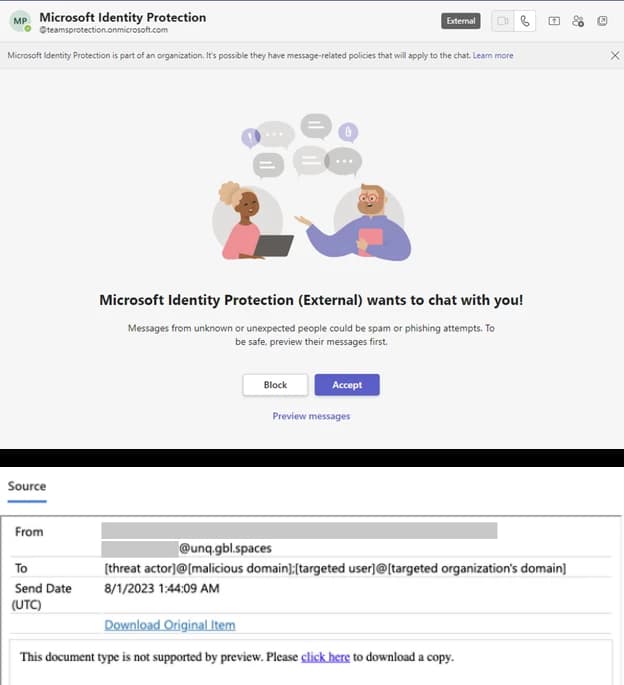
Russian hacking group Midnight Blizzard breached the UK Home Office, stealing sensitive data. Learn how they…

Try ThinLinc free for up to 10 concurrent users! Mention “NetworkChuck” for a special offer when…
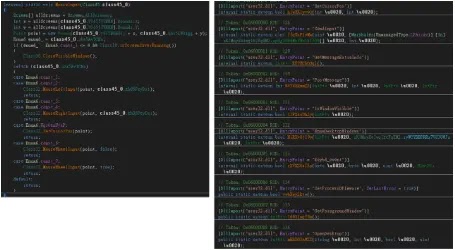
A sophisticated phishing campaign targeting Windows systems leverages multiple evasion techniques, including Python obfuscation, shellcode generation,…
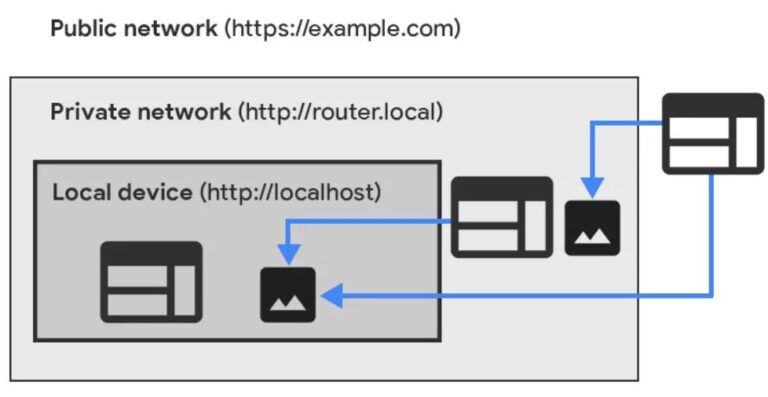
Threat actors often target and exploit security flaws in web browsers, as exploiting flaws in web…