Russian hacking group Midnight Blizzard breached the UK Home Office, stealing sensitive data. Learn how they exploited supply chain attacks to compromise government systems. Discover the urgent need for stronger cybersecurity measures.
The notorious Russian hacking group, Midnight Blizzard successfully infiltrated the UK government’s Home Office systems, stealing sensitive data and emails, a new report by The Record reveals.
As reported in January 2024, Midnight Blizzard compromised the email accounts of senior Microsoft executives and gained access to the company’s source code repositories and internal systems. Subsequently, the hackers leveraged this foothold to target Microsoft’s clients, including the UK Home Office.
The department reported the incident to the UK’s data protection regulator in May. In the report, obtained by The Record under the Freedom of Information Act, the department described the incident as a “nation-state attack on supplier” of its corporate systems and confirmed it was linked to the January attack targeting Microsoft.
In April, the US Cybersecurity and Infrastructure Security Agency (CISA) stated that the hack had also affected federal government data. Microsoft pledged to assist the US government’s investigation by providing metadata for all exfiltrated federal agency correspondence.
Microsoft has denied any compromise of customer-facing systems hosted by the company following the January attack, stating that the attacker only accessed a small percentage of Microsoft’s corporate email accounts and affected customers were notified.
The UK government has also denied any evidence of compromised operational Home Office data, stating that data security is taken seriously with robust reporting mechanisms and continuous monitoring.
Nevertheless, the incident highlights the growing sophistication and audacity of Midnight Blizzard. Hackread.com has been tracking the activities of this notorious group, which has emerged as a major threat, targeting a diverse range of organizations. Midnight Blizzard’s objectives are primarily espionage, targeting government entities, NGOs, IT services, technology, discrete manufacturing, and media sectors.
In June 2024, the group targeted TeamViewer, a German remote access and support software company, internal IT environment, possibly by exploiting compromised credentials of a standard employee account.
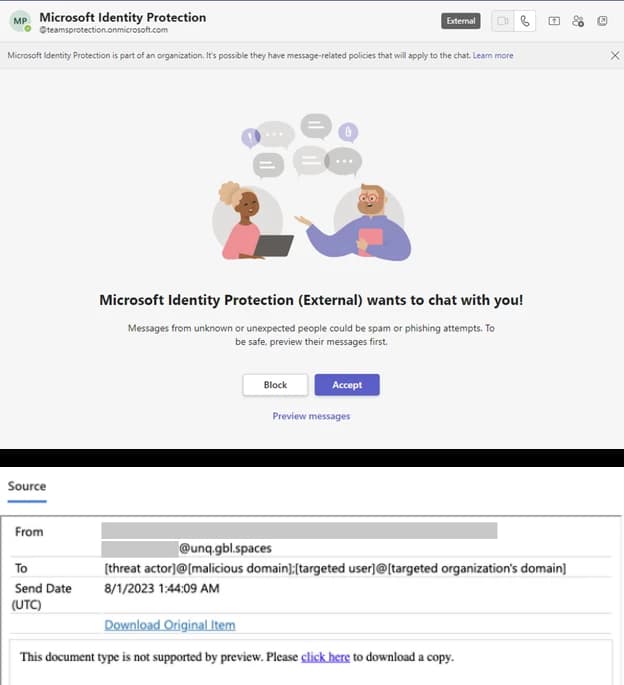
Microsoft recently reported a targeted social engineering attack by Midnight Blizzard, using phishing lures sent via Microsoft Teams chats to steal credentials, impacting at least 40 unique global organizations. These breaches raise serious concerns about the security of critical infrastructure and government systems.
This attack also raises questions about Microsoft’s security practices. Despite being a global tech giant, the company appears to have fallen victim to a basic security lapse by failing to implement multi-factor authentication on a non-production test tenant account, commented Kevin Robertson, COO of Acumen Cyber.
“This is yet another example of the dangerous monopoly Microsoft has on the digital world and how attackers are hijacking its ubiquity to compromise organisations,“ Kevin said. “In this attack, the threat actor leveraged an OAuth app within Microsoft’s test tenant, inadvertently granting it elevated permissions, which then provided access to Microsoft and its customers’ emails, including inboxes belonging to officials from the Home Office and the US government.“
RELATED TOPICS
- Fake Ledger App on Microsoft Store to Steal $800k in Crypto
- Microsoft Disables App Installer After It’s Abused for Malware
- Microsoft Azure Exploited to Create Undetectable Cryptominer
- Microsoft Teams External Access Abuses for DarkGate Malware
- Microsoft Outlook Flaw Exploited by Russian Forest Blizzard Group